Now that the creators of Flame have disclosed their product in a blatant sales pitch to attract would be customers, Crowdstrike wants sell you their solution and save the whole world. Why is CrowdStrike software already obsolete and worthless? Why should you avoid their products like the plague? Because the security industry is a racket and all they are looking to do is extort money for their products... and I will tell you why.
When was the last time you reverse-engineered all the PCI devices on your motherboard? After all it would be trivial for Intel to build in a back-door into their processors. Even something as simple as: "if (rax == MAGIC_1 && rcx == MAGIC_2) jmp [rbx]". It's actually worse than you think. A CPU is too complex for a human to design on the physical level, so we have to rely on software to do the design. This software could be compromised without the knowledge of an honest engineer. Back-doors can be installed directly into hardware components allowing root access to everything on the victims machine. There is no software solution to these kind of back-doors. In an ever changing dynamic digital world there is no final solution except to rely upon pencil and paper for all of your transactions. In the age of quantum entanglement even that won't get you very far. Yes even those neurophone implants that direct electromagnetic audio signals into the brains of IDF commanders in order for them to communicate De-facto telepathically aren't gonna save ya either, although it may cure deaf shell shock victims in the aftermath. The only temporary solution is to only use hardware manufactured and programmed with trusted components or to implement hardware based redundancies which render all potential back-doors null and void. Seeing that Intel is an Israeli based company, you should assume that there are hardwired back-doors in all civilian sector and non-domestic military products. Keeping in mind that once they finally decide to activate these back-doors to send information over a network, then it is all over for them... only during a time of war would the full extent of the damage caused by dormant unknown back-door variables become fully known. The outcome of any global war in the 21'st century will be determined predominately by digital means and the degree in which so-called leaders care more or less about everybody except themselves.
Even if ones personal computer hardware is technically clean off the assembly line, with a basic understanding of programmable language, a hacker could conceivably install a back-door into any piece of hardware that contains an expansion ROM, or on-board ROM boot-chip. Malware could be conceived that locates flashable hardware, saves a copy of the BIOS or firmware, and patches or re-flashes them with malicious code hooks, giving nearly undetectable hardware level access to intruders. This article explains in detail how by using a PCI card expansion ROM, and using only 200 bytes of code one can patch the kernel module of any Linux-distro and have complete administrator control over the computer at the hardware level leaving absolutely no traces on the computer. One would require hardware level anti-malware systems to detect such a back-door.
My computer was exhibiting the symptoms of a variant of Flame, which I documented here. During this time my video-card was overheating, crashing the computer repeatedly. The cards fan was completely out of control, speeding up and slowing down like it had a mind of its own. The only solution seemed to have been re-flashing the firmware which suggests that the virus may have been resident in the firmware or video-memory and hijacking the GPU. (Since the time of writing this article I've come across info suggesting that 'AMD has accused of poking holes in Windows security' and that quote, "Basically, that ATI driver has functionality that allows you to read and write kernel memory. It's either a bug or a feature of the driver. We're not sure why they're using it but because it's both signed and allowed to read/write kernel memory, any third party can use that driver to do the same thing" exposing OS kernel to hackers.
Wireless keyboard and mice signal's are easily intercepted... (Source)
When was the last time you reverse-engineered all the PCI devices on your motherboard? After all it would be trivial for Intel to build in a back-door into their processors. Even something as simple as: "if (rax == MAGIC_1 && rcx == MAGIC_2) jmp [rbx]". It's actually worse than you think. A CPU is too complex for a human to design on the physical level, so we have to rely on software to do the design. This software could be compromised without the knowledge of an honest engineer. Back-doors can be installed directly into hardware components allowing root access to everything on the victims machine. There is no software solution to these kind of back-doors. In an ever changing dynamic digital world there is no final solution except to rely upon pencil and paper for all of your transactions. In the age of quantum entanglement even that won't get you very far. Yes even those neurophone implants that direct electromagnetic audio signals into the brains of IDF commanders in order for them to communicate De-facto telepathically aren't gonna save ya either, although it may cure deaf shell shock victims in the aftermath. The only temporary solution is to only use hardware manufactured and programmed with trusted components or to implement hardware based redundancies which render all potential back-doors null and void. Seeing that Intel is an Israeli based company, you should assume that there are hardwired back-doors in all civilian sector and non-domestic military products. Keeping in mind that once they finally decide to activate these back-doors to send information over a network, then it is all over for them... only during a time of war would the full extent of the damage caused by dormant unknown back-door variables become fully known. The outcome of any global war in the 21'st century will be determined predominately by digital means and the degree in which so-called leaders care more or less about everybody except themselves.
My computer was exhibiting the symptoms of a variant of Flame, which I documented here. During this time my video-card was overheating, crashing the computer repeatedly. The cards fan was completely out of control, speeding up and slowing down like it had a mind of its own. The only solution seemed to have been re-flashing the firmware which suggests that the virus may have been resident in the firmware or video-memory and hijacking the GPU. (Since the time of writing this article I've come across info suggesting that 'AMD has accused of poking holes in Windows security' and that quote, "Basically, that ATI driver has functionality that allows you to read and write kernel memory. It's either a bug or a feature of the driver. We're not sure why they're using it but because it's both signed and allowed to read/write kernel memory, any third party can use that driver to do the same thing" exposing OS kernel to hackers.
Wireless keyboard and mice signal's are easily intercepted... (Source)
Conceivably manufacturing companies could hide back-doors inside wireless mice and keyboards, activating the back-door 'easter egg' via sending a 'cheat code' to the wireless receiver. Of course, the only people who would have VIP access to this kind of information are the moles programming and manufacturing the components, inserting them into the post-production line, and of course those with the motivation and money to implement these hardwired bugs in the first place.
If you don't think that manufactures would be willing to go to such lengths, keep in mind that manufacturers in Taiwan were caught producing external drives with a Trojan virus pre-installed on them which transmitted any data saved on the drives to online servers. In 2006 Apple manufactured an IPod with a Trojan virus pre-installed. Chinese manufactures are well known to manufacture counterfeit chips that on behalf of the US military, wound up installed in critical US military equipment.
If you don't think that manufactures would be willing to go to such lengths, keep in mind that manufacturers in Taiwan were caught producing external drives with a Trojan virus pre-installed on them which transmitted any data saved on the drives to online servers. In 2006 Apple manufactured an IPod with a Trojan virus pre-installed. Chinese manufactures are well known to manufacture counterfeit chips that on behalf of the US military, wound up installed in critical US military equipment.
In April of 2012 RuggedCom, a Canadian based critical communications infrastructure manufacturer recently bought up by Siemens, in one of the most alarming revelations in the IT world, was discovered to have been manufacturing software with a hardwired back-door easily accessible to anybody with the elementary know-how.
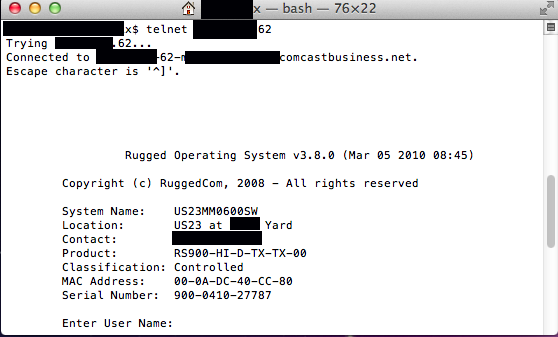
"equipment running RuggedCom's Rugged Operating System has an undocumented account that can't be modified and a password that's trivial to crack. What's more, researchers say, for years the company hasn't bothered to warn the power utilities, military facilities, and municipal traffic departments using the industrial-strength gear that the account can give attackers the means to sabotage operations that affect the safety of huge populations of people."
"It is esoteric, it is obscure, but this equipment is everywhere," he said. "I was walking down the street and they had one of the traffic control cabinets that controls stop lights open and there was a RuggedCom switch, so while you and I may not see it, this is what's used in electric substations, in train control systems, in power plants and in the military. That's why I personally care about it so much."
"The US Navy, the Wisconsin Department of Transportation, and Chevron are just three of the customers who rely on the gear, according to this page on RuggedCom's website."
"The backdoor uses the login ID of "factory" and a password that's recovered by plugging the MAC, or media access control, address of the targeted device into a simple Perl script, according to this post published on Monday to the Full Disclosure security list. To make unauthorized access easy, paying customers of the Shodan computer search engine can find the IP numbers of more than 60 networks that use the vulnerable equipment. The first thing users who telnet into them see, as the picture above demonstrates, is its MAC address." (Source)
-Ed Note, Just take a glimpse at that last link, search for a power plant, police station, or oil refinery and you will have an idea of just how vulnerable the world is thanks to corporations like Siemens.
"Programmable logic controllers like these are used to operate machinery used in refineries and other critical infrastructure. Despite their sensitivity, manufacturers often decline to fix software flaws that could allow the devices to be remotely hijacked."
Quote, "Other forever day vulnerabilities date back as far as six years. A plugin added to the Nessus security scanner in 2006, for example, targets an FTP server that ships with the Modicon Quantum, a programmable logic controller made by Schneider-Electric. More than six years later, the back-door accounts hard-coded into the device remain.
Another buggy PLC that won't be fixed anytime soon is the Siemens's SIMATIC controller used in plants in the water, wastewater, oil, gas, and chemical industries. According to an advisory issued in September, "Siemens currently has no plans to patch this vulnerability," which stemmed from an overflow that could allow attackers to execute arbitrary code on the targeted human-machine interface system.
Earlier this year, researchers discovered a series of additional vulnerabilities in the same product. Some of them, including default administrator passwords that are easy to recover, remain unfixed. Instead, "Siemens has changed the documentation to encourage users to change the password at first login." (source)
It should come as no surprise that Siemens colluded with the US and Israel to create the Stuxnet worm which was detected all across Japan months before the disaster at Fukushima.
While the US military is searching for Chinese built kill-switches in their junkware in their quest to massacre another innocent nation that actually knows how to run a country, and are not subservient to a Rothschild controlled private central bank...
The Hunt for the Kill Switch (source)
"Are chip makers building electronic trapdoors in key military hardware? The Pentagon is making its biggest effort yet to find out."
(cont)...Intel's new Sandy Bridge & Ivy architecture is openly sold with a built in remote kill switch and drive wiper that could be flipped at the discretion of the Rothschild crime syndicate even if the computer has no Internet connection or isn't even turned on. The new lineup even has a convenient remote BIOS back-door sold as a 'feature.'
Everything can be reverse engineered and hacked eventually... how long will it be before someone other than "Israel" gets their hands on the code to kill the CPU's? Is there any hands out there that could be worse than these people? Perhaps openly selling products with back-doors is an attempt to avoid class action lawsuits against their company when they decide to proactively disengage anti-asshole dissidents while they continue their legacy of corporate espionage. If the general public doesn't hack the code first, the hook nosed black hats at Intel will certainly sell their secrets in due time, anything for a shekel.
 The world public should file a class action lawsuit against Siemens and RuggedCom. The only way to prevent these problems is to hit the perpetrators where it hurts, in the pocket... even if it simply means walking away from their crapware. Israeli's don't like chess. It would appear that the ideal world of the Zionist banker is to have the all of humanity running everything from one centralized monolithic power grid... a kind of high stakes game of Ganga where if you remove even the most redundant part, the entire system comes crashing down. Israel likes to call it the Sampson option. All the safety mechanisms that could create a worthwhile product have been thrown out the window. Anybody who believes in good faith that Microsoft, Intel, and Crowdstrike, or any of these security racketeers will protect you are wasting their breath and flirting with the loss of everything they seek to protect. Its a two tiered system. Israel is actively seeking to ensure that every weapons targeting system in the world has an un-hackable IFF (Identification Friend or Foe) no-friendly-fire system implemented to protect the Jewish state, even if it means self-destruction of the unit. Can Israel be certain that their own Submarines, Aircraft, Missiles and Tanks are not riddled with ticking time-bombs and back-doors? I am betting on the unexpected.
The world public should file a class action lawsuit against Siemens and RuggedCom. The only way to prevent these problems is to hit the perpetrators where it hurts, in the pocket... even if it simply means walking away from their crapware. Israeli's don't like chess. It would appear that the ideal world of the Zionist banker is to have the all of humanity running everything from one centralized monolithic power grid... a kind of high stakes game of Ganga where if you remove even the most redundant part, the entire system comes crashing down. Israel likes to call it the Sampson option. All the safety mechanisms that could create a worthwhile product have been thrown out the window. Anybody who believes in good faith that Microsoft, Intel, and Crowdstrike, or any of these security racketeers will protect you are wasting their breath and flirting with the loss of everything they seek to protect. Its a two tiered system. Israel is actively seeking to ensure that every weapons targeting system in the world has an un-hackable IFF (Identification Friend or Foe) no-friendly-fire system implemented to protect the Jewish state, even if it means self-destruction of the unit. Can Israel be certain that their own Submarines, Aircraft, Missiles and Tanks are not riddled with ticking time-bombs and back-doors? I am betting on the unexpected. While the evidence of what happened in the Gulf bubbles up from the bottom of the deep blue sea, and the evidence of what happened in Fukushima lies bleeding into the pacific, we can assume that any suspicious occurrence ranging from hardware malfunctions of stop lights at highway intersections, to aircraft crashes, to car accidents, to hardware failures, to monolithic industrial disasters like Fukushima and the Gulf oil spill are the result of greed driven corporate espionage caused by time-bombs and back-doors built into hardware components. Planned obsolescence may be a better term in many instances... anything so the "donkey's" continue coming back for a shekel, as Rabbi Ovadia Yosef in Israel would say. "Better buy our crapware or somethin bad gonna happen to ya."
In 2007, when the Israeli air force invaded Syria and destroyed the al-Kibar site, Israel alleged that the site was harboring a nuclear reactor... however, subsequent inspections by the IAEA proved once again that every accusation coming from the usurping Jewish entity is a fabricated lie. Some reports suggest that Syrian air radars malfunctioned during this period because of? You guessed it, a built in back-door within the CPU's used to power them. Meanwhile the IDF unit involved with the development of Fuku-Stuxnet is pushing forward both offensive and defensive cyber warfare exercises, "establishing offensive capabilities and operations within Military Intelligence’s Unit 8200 and defensive operations in the C4I Directorate’s Cyber Defenders Division."
And this brings me onto the next bit. I am beginning to suspect that Flame and other similar malware is downloaded directly from Microsoft's servers onto target specific machines as the Jewish mafia increases their cyber espionage activities against civilized nations and activists around the globe.
Could US cyberspies have moles inside Microsoft?Source
Quote, "US government officials could be working under cover at Microsoft to help the country's cyber-espionage programme, according to one leading security expert. The warning comes in the wake of the Flame virus that targeted key computers in the Middle East, and in part used confidential Microsoft certificates in order to access machines. According to Mikko Hypponen, chief research officer at security firm F-Secure, the claim is a logical conclusion to a series of recent discoveries and disclosures linking the US government to 2010's Stuxnet attack on Iran and ties between Stuxnet and the recent Flame attack."
“The announcement that links Flame to Stuxnet and the conclusive proof that Stuxnet was a US tool means that Flame is also linked to the US government,” Hypponen said.
It's plausible that if there is an operation under way and being run by a US intelligence agency it would make perfect sense for them to plant moles inside Microsoft “This makes you think that this breach of Microsoft's update system was done by the Americans and most likely a US agency, someone like the NSA,” Hypponen said.
“That must make Microsoft mad as hell that its most critical system, used by 900 million of its customers, was breached by fellow Americans.” End Quote.
Keep in mind that that F-Secure and other security companies claim to have had samples of Flame for years, but have done absolutely nothing about it, "Mikko Hypponen, the well-regarded chief research officer at Finland’s F-Secure Oyj, told the Reuters Summit his company had a sample of Flame in 2010 and classified it as clean" Source

Microsoft hands NSA access to encrypted messages: Report

New leaks by American
whistleblower Edward Snowden show that Microsoft cooperated with the United
States to give the National Security Agency access to the internet giant's
encrypted data.The Guardian reported the top
secret documents show that Microsoft gave the Federal Bureau of Investigation
and the NSA access to Skype video calls, Outlook and Hotmail accounts.
The main points as summarized in
the Guardian:
• Microsoft helped the NSA to circumvent its
encryption to address concerns that the agency would be unable to intercept web
chats on the new Outlook.com portal;
• The agency already had pre-encryption stage access
to email on Outlook.com, including Hotmail;
• The company worked with the FBI this year to allow
the NSA easier access via Prism to its cloud storage service SkyDrive, which now
has more than 250 million users worldwide;
• Microsoft also worked with the FBI's Data
Intercept Unit to "understand" potential issues with a feature in Outlook.com
that allows users to create email aliases;
• Skype, which was bought by Microsoft in October
2011, worked with intelligence agencies last year to allow Prism to collect
video of conversations as well as audio.
The company had previously denied
helping the NSA. Microsoft said in a statement on Thursday that it only gave up
customer data when it was done through government requests.
"To be clear, Microsoft does not provide any
government with blanket or direct access to SkyDrive, Outlook.com, Skype or any
Microsoft product," the company said.
"There are aspects of this debate that we wish we
were able to discuss more freely. That’s why we’ve argued for additional transparency that
would help everyone understand and debate these important issues."
Former NSA contractor Snowden, who is charged with espionage, is reportedly staying at Moscow's Sheremetyevo International Airport. Earlier documents disclosed by Snowden revealed massive surveillance by the NSA including two major spying programs, one for gathering U.S. phone records and another, called PRISM, for tracking the use of U.S.-based web servers by American citizens and other nationals. Other documents have also shown that the U.S. government spied on European Union offices and Brazilian companies and individuals. (Source)
Flame was detected in Hungary, Russia, and Iran only a month prior to the time of this writing. This suggests that major security firms were working in collusion with the US and Israeli governments to remain silent about these weapons of mass destruction. Stuxnet was detected all across Japan just prior to the Fukushima disaster in which the emergency cooling systems of the Fukushima rectors failed to activate properly. In fact, an Israeli firm was in charge of security at the Fukushima plant during the time of the disaster. Iran and Japan should launch a joint investigation into this matter to see if the Jewish security firm and software created by these rogue intelligence agencies were the root cause for the greatest nuclear disaster in human history. Latest reports indicate that Cesium 137 has been detected in some ~95% of the urine samples of individuals living within 200 kilometers from the Fukushima disaster area.
NSA spying never catches Israelis - Why not?

(source)
In 2011 Microsoft handed contracts to Israeli based firms to provide low level networking components in Windows 8. Talk about your chutzpah:
Israel's Mellanox to Drive Windows Server 8, providing InfiniBand and Ethernet components to drive core Windows Server 8 functionality. Source
Microsoft has been colluding with the FBI and other intelligence agencies for years now.
Quote, "Back in 2008, Microsoft provided the U.S. government a technical “backdoor” to its browser, which serves the majority of users (over 60%). Backdoor access is undetectable by security software—it bypasses normal authentication (passwords, etc.), firewalls and other computer security devices. In other terms, the Department of Justice, Homeland Security, the FBI and other security agencies can already eavesdrop on anyone using Microsoft’s Internet Explorer browser."(Source)

One module of Flame reportedly records and stores Skype conversations on victims computers and uploads the content to 'command and control' servers on the Internet. Just days ago, Microsoft's windows update service installed Skype onto unsuspecting victims computers without their consent. Microsoft MVP Lawrence Garvin confirmed yesterday that when leaving automatic updates enabled on your windows machine that quote "You have no control over what is installed -- right or wrong." If in fact Flame was a collaborative effort involving rouge elements within Microsoft as suspected, then we should expect that flame could very well be installed onto target specific machines directly from Microsoft's own servers. One source recently suggested that "the creators of these viruses have apparently managed to plant them on any PC they wanted to." How do they know?
Who is behind flame? Ever heard of Crowdstrike?
“We will have a world government whether you like it or not. The only question is whether that government will be achieved by conquest or consent.”
—Jewish International Banker James Warburg on February 17, 1950, as he testified before the U.S. Senate. James was the son of Paul Warburg, who represented the Rothschilds when they created the Federal Reserve act at Jekyll Island in 1910. He also later formed the Council of Foreign Relations (CFR). Remember him the next time you wonder why the dollar is so worthless.
CrowdStrike is a gang of security veterans with direct ties to the Warburg crime family, J.P Morgan and other major criminal financial firms working in collusion with elements within US Government, FBI, CIA, Private, and Israeli Military Intelligence Unit 8200 and defensive operations in the C4I Directorate’s Cyber Defenders Division, Microsoft, Mcafee, Google...etc.
Elements of the CrowdStrike team oversaw cyber espionage directed against China in recent years. Remember the debacle about Googles hacking allegations against China? Operation Aurora, Night Dragon, and Shady RAT in which these Jewish criminals constantly cried out in pain when they strike their victims? Keep in mind that Joogle itself is a tribe enterprise, read: The Jewish hand behind Internet - Google, Facebook, Wikipedia, Yahoo!, MySpace, eBay.
Quote "Operation Aurora was a cyber attack which began in mid-2009 and continued through December 2009. The attack was first publicly disclosed by Google on January 12, 2010, in a blog post. In the blog post, Google said the attack originated in China. The attacks were both sophisticated and well resourced and consistent with an advanced persistent threat attack." snip "As a result of the attack, Google stated in its blog that it plans to operate a completely uncensored version of its search engine in China "within the law, if at all", and acknowledged that if this is not possible it may leave China and close its Chinese offices. Official Chinese media responded stating that the incident is part of a U.S. government conspiracy." Source
Of course, citing a link directly from CrowdStrike's website "Google would like you to think of them as the dolphin in a vendor sea full of sharks. snip -But what they won’t do is hold your hand when you’re drowning in technical issues."
Maimonides, Mishnah Torah, (Moznaim Publishing Corporation, Brooklyn, New York, 1990, Chapter 10, English Translation), p. 184: "Accordingly, if we see an idolater (gentile) being swept away or drowning in the river, we should not help him. If we see that his life is in danger, we should not save him." The Hebrew text of the Feldheim 1981 edition of Mishnah Torah states this as well.They create the problem, blame the victim, and claim to offer a viable solution, for a shekel of course... Co-Founder & CTO of CrowdStrike, Dmitri Alperovitch claims that "Some victims (China in particular) seem determined to deny they’ve been attacked, even when offered empirical proof that a smash-and-grab has taken place." ed note: Who could have proof of these so called smash and grab's but the people behind the them in the first place? China wont let these clowns near them.
"Don't worry, there is a ray of hope, CrowdStrike vows to Save the World From Flame Malware" Source
All these people seem to be useful for is creating more and more problems. Even in the aftermath of the greatest man made disasters in history like Fukushima, they don't care... they project their incompetence on to people who actually know how to run a nation properly. In fact Israel want's to see the same thing that happened at Fukushima happen to Iranians... nuke Iran's peaceful Nuclear power facilities and irradiate their ~80,000,000 population. This sick and diseased mindset cares souly on the acquisition of temporary profits at the expense of others and anything of any real lasting value. Human civilization as we have known it could be living in a kind of garden of Eden at this time, yet it is teetering on the brink of utter disaster because the people who think they know whats best for you are more concerned about creaming every last bit of imaginary profit from a dying empire than contributing to a future worth living in. The people behind these crimes must be stopped and brought to justice before they take the civilized world down with them.
If you want security, I recommend checking out China's new Loongson CPU product line... hopefully Iran will start printing out their own CPU's for the general public as well.